Some use cases¶
As a framework, IVRE has several possible use cases. Of course, you probably want to use only parts of what IVRE can do.
Your own Shodan / ZoomEye / Censys / Binaryedgeio / whatever¶
You can use IVRE as a private (or even public, if you want) alternative to Shodan (or any other similar service).
The main difference with public services is that you will have the control of your data. You can scan whatever you want (your private networks, public networks, a specific country or Autonomous System, the whole Internet, etc.), for any port or protocol. You can run any query on your data; no-one has to know what you are really looking for.
Of course, this require more work than just using an existing public service, but the benefits are huge!
IVRE does not come with a scanner, and takes advantage of Nmap, Masscan and Zgrab / Zgrab2. Depending on your use case, you can choose one
or use both (IVRE will happily merge the results for you). Remember to
use the -oX option (which works with both Nmap and Masscan) or
-o for Zgrab2, as IVRE needs the XML output file for Nmap and
Masscan, and JSON for Zgrab2.
You can use ivre runscans, ivre runscansagent or
ivre runscansagentdb to run Nmap scans against wide targets (more)
easily.
You will then store the results from the XML or JSON output files into
IVRE database using ivre scan2db.
Finally, use ivre db2view nmap to create a view (see
Purposes) that you can explore with the
Web User Interface.
See IVRE with Kibana if you want to use Kibana to explore your scan results.
Your own Passive DNS service¶
Passive DNS services log DNS answers into a database and let you run queries against them.
IVRE uses its Zeek script passiverecon
to, among others, log DNS answers. They are stored in the passive
purpose (see Purposes) via ivre
passiverecon2db CLI tool as DNS_ANSWER records.
They can be queried using ivre iphost CLI tool, as in the
following example (the results come from a PCAP file used in IVRE’s
Tests):
$ ivre iphost ipv4.icanhazip.com
ipv4.icanhazip.com A 216.69.252.101 (109.0.66.10:53, 1 time, 2014-01-02 09:37:57.197000 - 2014-01-02 09:37:57.197000)
ipv4.icanhazip.com A 216.69.252.100 (109.0.66.10:53, 1 time, 2014-01-02 09:37:57.197000 - 2014-01-02 09:37:57.197000)
ipv4.icanhazip.com A 216.69.252.100 (109.0.66.20:53, 1 time, 2014-01-02 09:37:57.197000 - 2014-01-02 09:37:57.197000)
ipv4.icanhazip.com A 216.69.252.101 (109.0.66.20:53, 1 time, 2014-01-02 09:37:57.197000 - 2014-01-02 09:37:57.197000)
$ ivre iphost 216.69.252.101
ipv4.icanhazip.com A 216.69.252.101 (109.0.66.10:53, 1 time, 2014-01-02 09:37:57.197000 - 2014-01-02 09:37:57.197000)
ipv4.icanhazip.com A 216.69.252.101 (109.0.66.20:53, 1 time, 2014-01-02 09:37:57.197000 - 2014-01-02 09:37:57.197000)
To see an interactive session of IVRE using passive data (including DNS answers), have a look at Passive network analysis.
YETI plugin¶
Yeti is a platform meant to organize observables, indicators of compromise, TTPs, and knowledge on threats in a single, unified repository.
It comes with an “analytics” plugin that uses IVRE’s data to create links between IP addresses, hostnames, certificates, etc.
To learn more about this plugin, have a look at its documentation.
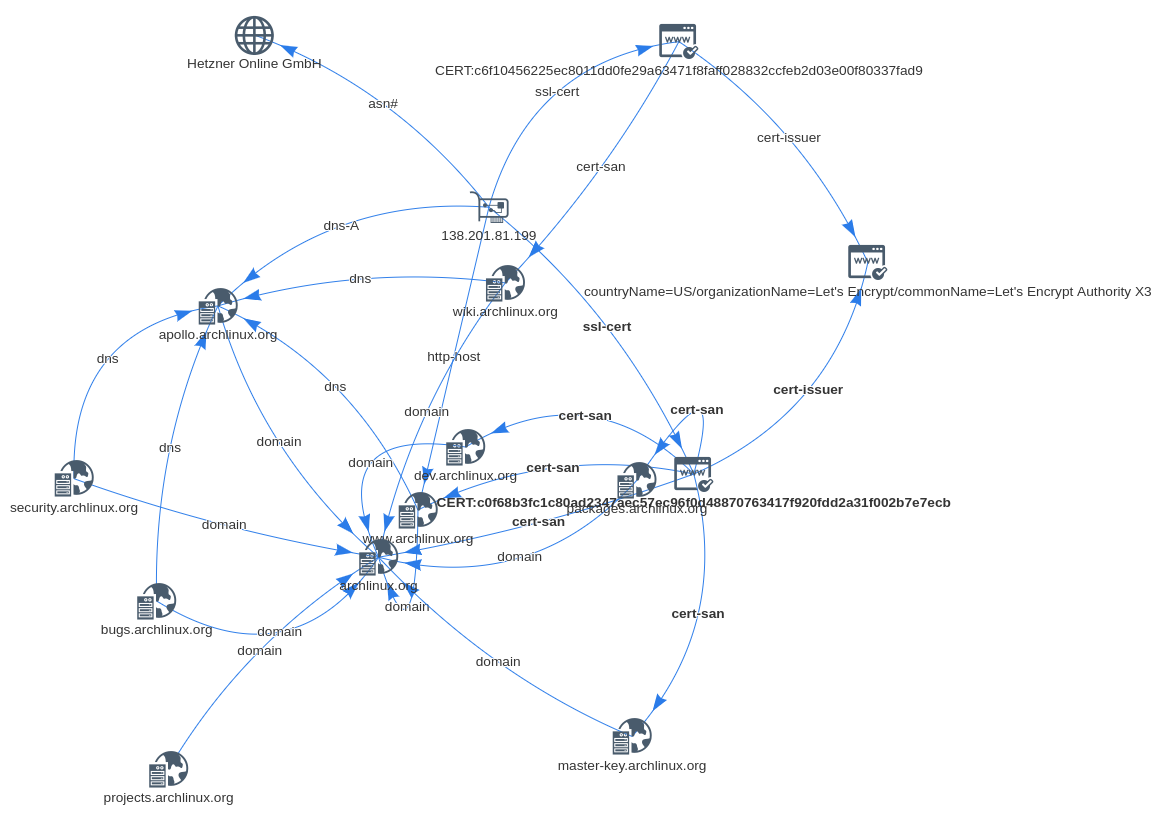
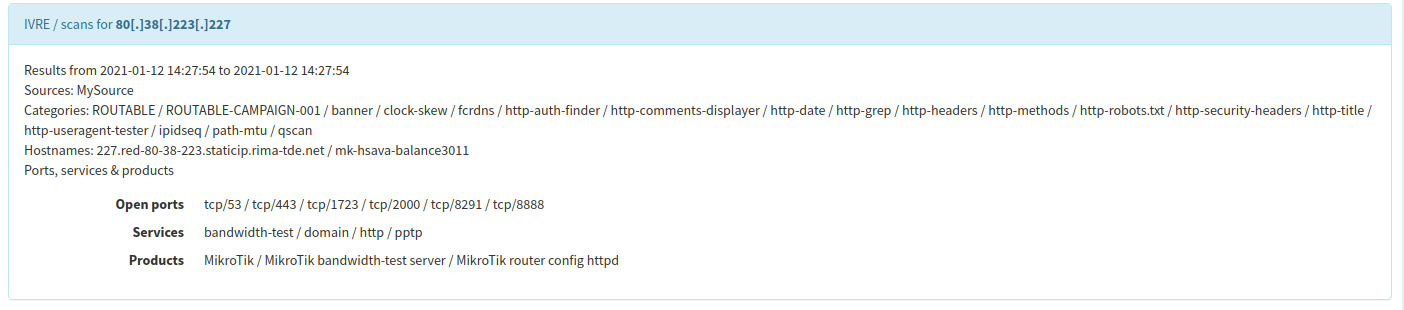
Cortex analyzer¶
Cortex is a tool to analyze observables for SOCs, CSIRTs and security researchers; it integrates well with TheHive.
It comes with an “Analyzer” that uses IVRE’s data to report intelligence about Autonomous Systems, certificates, domain and host names, IP addresses, networks, open ports, etc.
To learn more about this analyzer, have a look at its documentation.
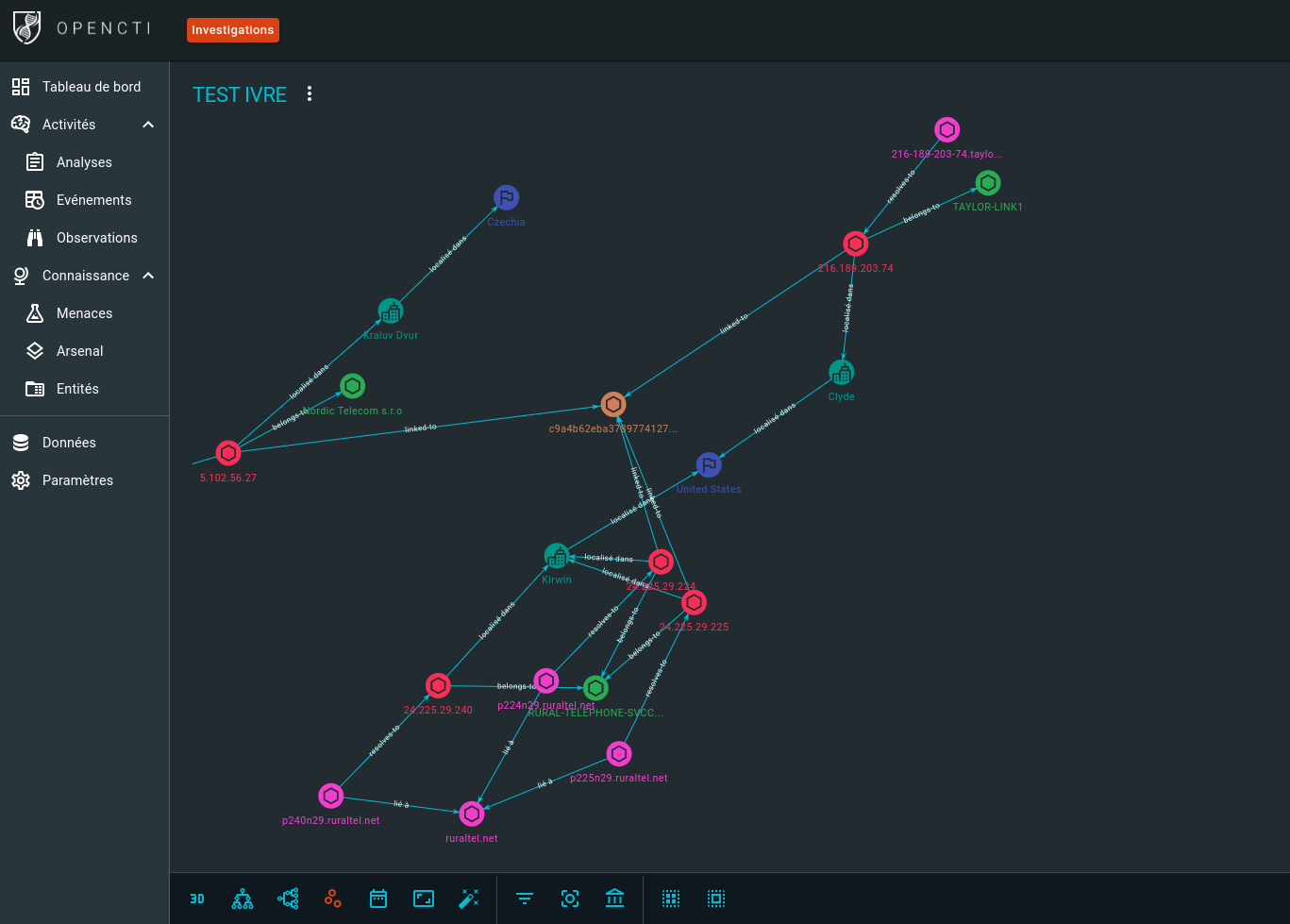
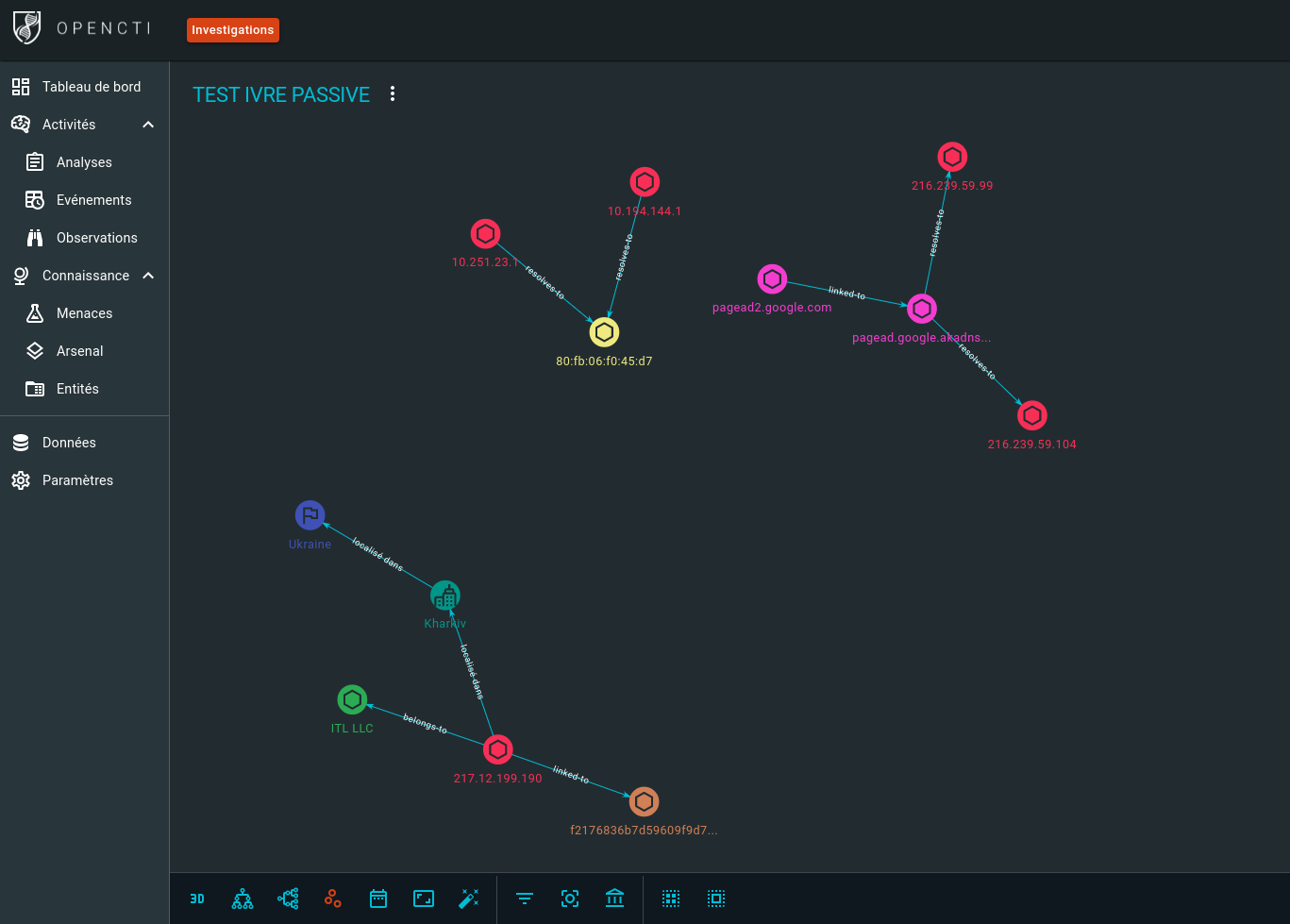
OpenCTI connector¶
OpenCTI is an open-source cyber threat intelligence (CTI) platform.
It comes with an “internal enrichment connector” that uses IVRE’s data to create links between IP addresses, MAC addresses, hostnames, certificates, AS numbers and locations.
To learn more about this connector, have a look at its documentation.
Obsidian plugin¶
Obsidian is a knowledge base and note-taking application that relies on Markdown files.
A community plugin exists that uses IVRE’s data to create notes based on IVRE’s data that provides context to your notes related to pentest or red team engagements, bug bounty hunting, cyber threat intelligence, etc.
See the plugin’s README.

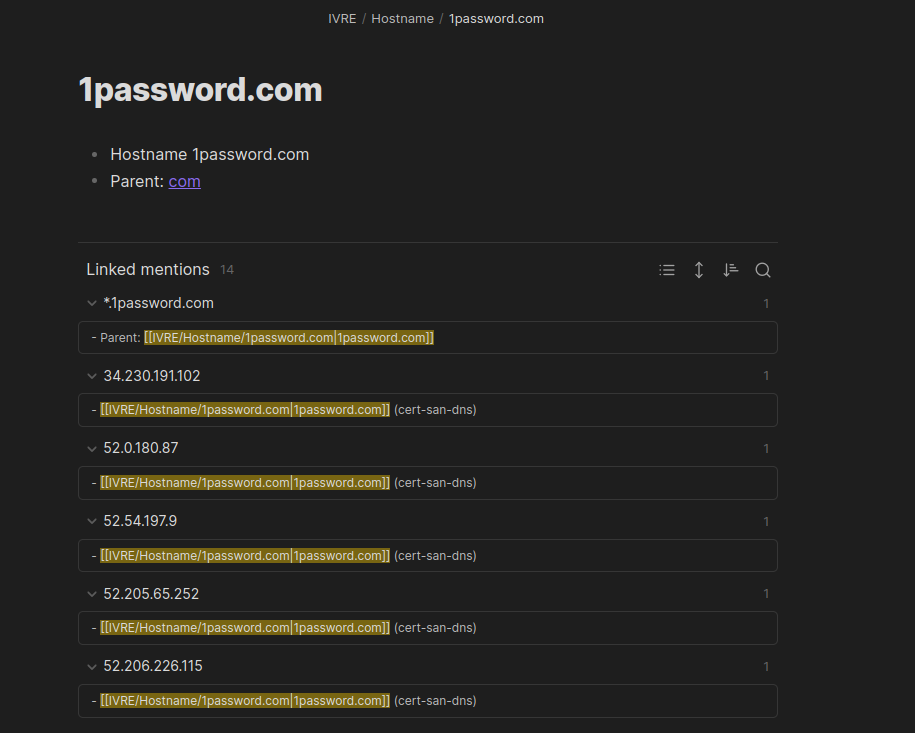
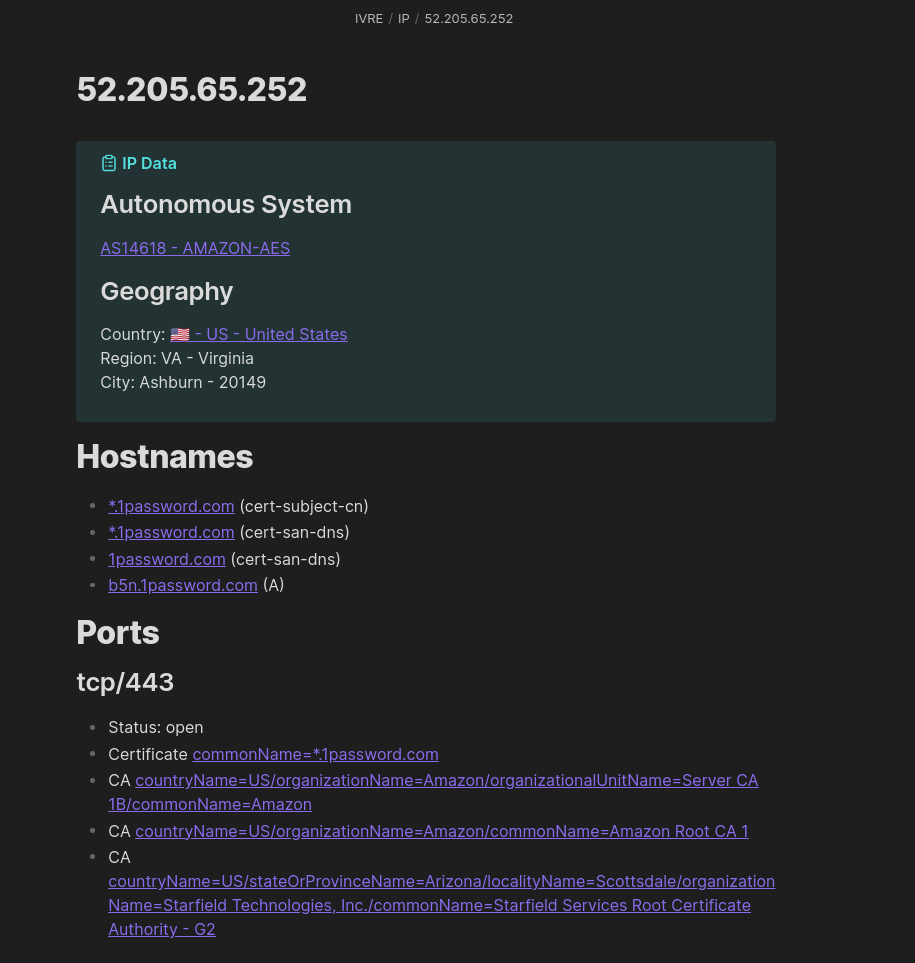
Blog posts and other resources¶
The author’s blog has some IVRE-related blog posts that might be useful.
Here is a list of other blog posts about or around IVRE:
External attack surface monitoring:
Scan the hosts that hit your honeypots, and exploit the results!
Scanning SAP Services:
IVRE tests & reviews:
Spanish:
You have found (or written) a document that might help other use IVRE or decide if they need it? Please let us know: open an issue or Contact us so that we can add a link here!